So, it’s your turn!
Your sites are going under attack unless you pay 25 Bitcoin.
“DD4BC”

So, it’s your turn!
Your sites are going under attack unless you pay 25 Bitcoin.
“DD4BC”
One day a system administrator of one of our client got an extraordinary e–mail.
Guys from so–called “DD4BC” group treatened the company to start powerfull DDOS attack on the compay’s site. They wanted money and gave the company a day.
“Your sites are going under attack unless you pay 25 Bitcoin.”
“[…]we are giving you 24 hours to get it and pay us.”
they wanted 25 Bitcoins to a predefine account. Obviouly nonbody replied or paid them.
Statistics on botnet–assisted DDoS attacks in Q1 2015 (excerpts from securelist.com):
Next day the DDoS-ing started as they promised.
The attackers used IP addresses as targets for UDP amplification DDoS attack against customer’s uplinks, so we used BGP blackhole communities to discard traffic at Edge routers of upstream Tier1 ISPs.
Taking into account difference between average daily traffic and traffic when DDoS-ing, we were getting approximally 100 GBit/sec load on the network. Traffic dump shown ~120.000 infected nodes that were producing the DDoS attack itself. This impresses a lot and shows that an average DDoS-er has such considerable resource in hand.
The attack was beaten in 10 minutes. The attackers had an IP address as a target for DDoS-ing, so we used BGP protocol to redirect attackers to nowhere:
That’s all. If you have the same troubles with attackers, call us. We help.
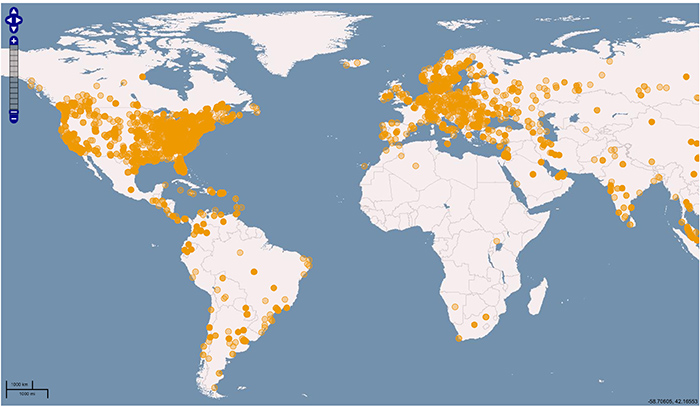
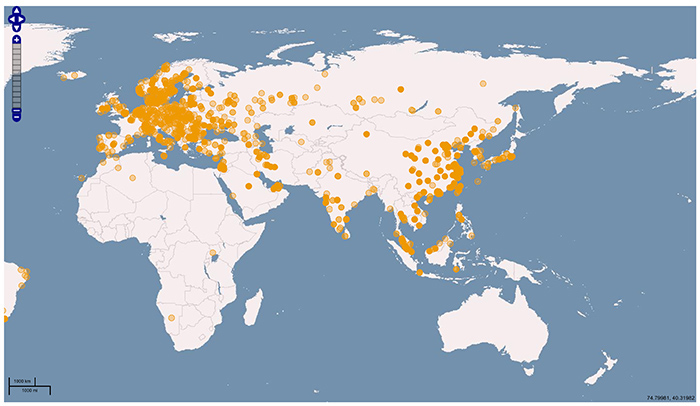
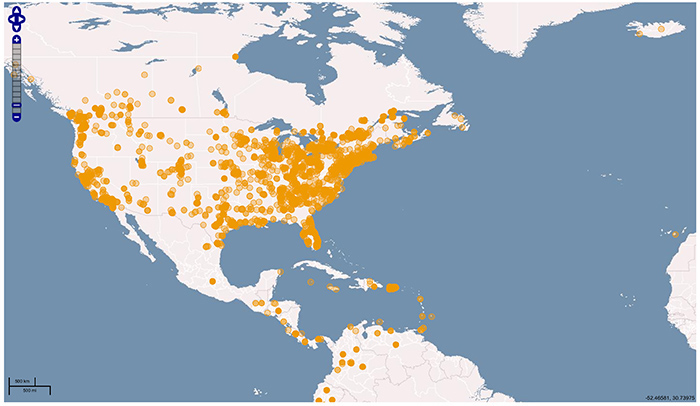
Here you can see geography of the hosts used for UDP amplification attack: